Three restaurant ordering platforms MenuDrive, Harbortouch, and InTouchPOS were the target of two Magecart skimming campaigns that resulted in the compromise of at least 311 restaurants.
The trio of breaches has led to the theft of more than 50,000 payment card records from these infected restaurants and posted for sale on the dark web.
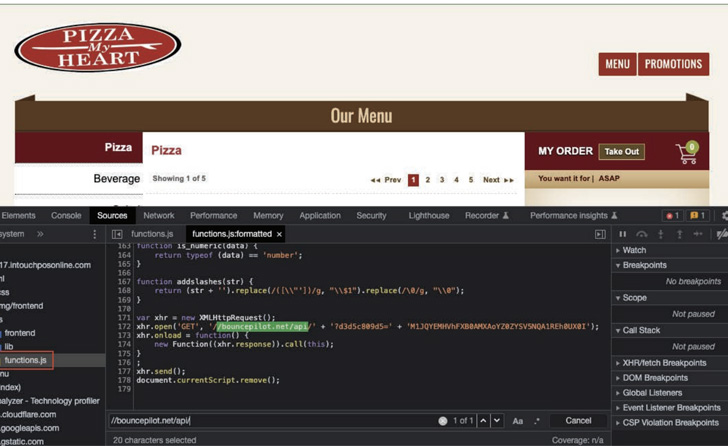
“The online ordering platforms MenuDrive and Harbortouch were targeted by the same Magecart campaign, resulting in e-skimmer infections on 80 restaurants using MenuDrive and 74 using Harbortouch,” cybersecurity firm Recorded Future revealed in a report.
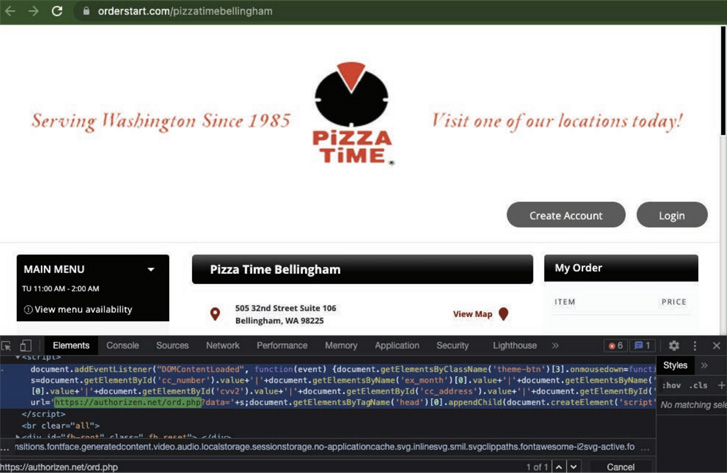
“InTouchPOS was targeted by a separate, unrelated Magecart campaign, resulting in e-skimmer infections on 157 restaurants using the platform.”
Magecart actors have a history of infecting e-commerce websites with JavaScript skimmers to steal online shoppers’ payment card data, billing information, and other personally identifiable information (PII).
The first set of activities is believed to have started around January 18, 2022, and continued until the malicious domain used in the campaign was blocked on May 26. The InTouchPOS campaign, on the other hand, has remained active since November 12, 2021.
It’s worth noting that the data exfiltration domain used in the infections of MenuDrive and Harbortouch has also been identified by the U.S. Federal Bureau of Investigation (FBI) in a May 2022 flash alert.
The attacks entail inserting malicious PHP code into the businesses’ online checkout pages by taking advantage of known security flaws in the services to scrape and transmit the customer data to a server under the attacker’s control.
The idea is that by targeting online ordering platforms, it can lead to a scenario where when even a single platform is attacked, dozens or even hundreds of restaurants can have their transactions compromised, which enables “cybercriminals to steal vast amounts of customer payment card data disproportionate to the number of systems they actually hack.”
The development is significant for a number of reasons. First, the intrusions are a departure from the threat actor’s traditional targeting of the Magento e-commerce platform, a fact exemplified by the uptick in skimmer attacks aimed at a WordPress plugin named WooCommerce.
Furthermore, it serves to highlight how Magecart campaigns are now singling out small, local restaurants that rely on third-party software from lesser-known online ordering services in lieu of designing their own checkout web pages, effectively widening the pool of attack vectors.
“Centralized ordering platforms servicing multiple merchants offer a unique opportunity for Magecart threat actors to collect customer PII and payment card data,” the researchers said. “Cybercriminals’ increasing interest in targeting online ordering platforms represents a new dimension of risk for restaurants.”