A Chinese-speaking advanced persistent threat (APT) actor codenamed MirrorFace has been attributed to a spear-phishing campaign targeting Japanese political establishments.
The activity, dubbed Operation LiberalFace by ESET, specifically focused on members of an unnamed political party in the nation with the goal of delivering an implant called LODEINFO and a hitherto unseen credential stealer named MirrorStealer.
The Slovak cybersecurity company said the campaign was launched a little over a week prior to the Japanese House of Councillors election that took place on July 10, 2022.
“LODEINFO was used to deliver additional malware, exfiltrate the victim’s credentials, and steal the victim’s documents and emails,” ESET researcher Dominik Breitenbacher said in a technical report published Wednesday.
MirrorFace is said to share overlaps with another threat actor tracked as APT10 (aka Bronze Riverside, Cicada, Earth Tengshe, Stone Panda, and Potassium) and has a history of striking companies and organizations based in Japan.
Indeed, a pair of reports from Kaspersky in October 2022 linked LODEINFO infections targeting media, diplomatic, governmental and public sector organizations, and think-tanks in Japan to Stone Panda.
ESET, however, said it hasn’t found evidence to tie the attacks to a previously known APT group, insteading tracking it as a standalone entity. It also described LODEINFO as a “flagship backdoor” exclusively used by MirrorFace.
The spear-phishing emails, sent on June 29, 2022, purported to be from the political party’s PR department, urging the recipients to share the attached videos on their own social media profiles to “secure victory” in the elections.
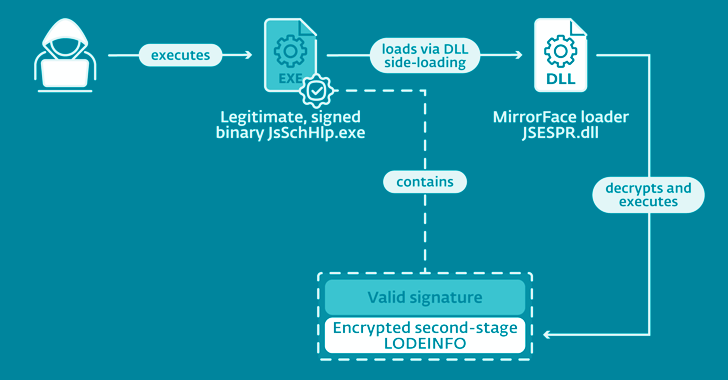
However, the videos were self-extracting WinRAR archives designed to deploy LODEINFO on the compromised machine, allowing for taking screenshots, logging keystrokes, killing processes, exfiltrating files, and executing additional files and commands.
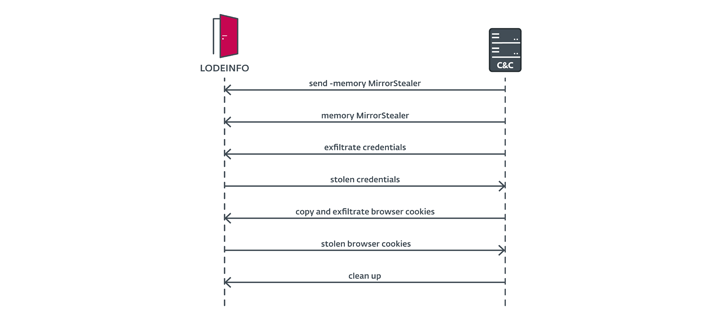
Also delivered was the MirrorStealer credential grabber that’s capable of plundering passwords from browsers and email clients like Becky!, which is primarily used in Japan.
“Once MirrorStealer had collected the credentials and stored them in %temp%31558.txt, the operator used LODEINFO to exfiltrate the credentials,” Breitenbacher explained, since it “doesn’t have the capability to exfiltrate the stolen data.”
The attacks further made use of a second-stage LODEINFO malware that comes with capabilities to run portable executable binaries and shellcode.
“MirrorFace continues to aim for high-value targets in Japan,” ESET said. “In Operation LiberalFace, it specifically targeted political entities using the then-upcoming House of Councillors election to its advantage.”