An analysis of new samples of BlackMatter ransomware for Windows and Linux has revealed the extent to which the operators have continually added new features and encryption capabilities in successive iterations over a three-month period.
No fewer than 10 Windows and two Linux versions of the ransomware have been observed in the wild to date, Group-IB threat researcher Andrei Zhdanov said in a report shared with The Hacker News, pointing out the changes in the implementation of the ChaCha20 encryption algorithm used to encrypt the contents of the files.
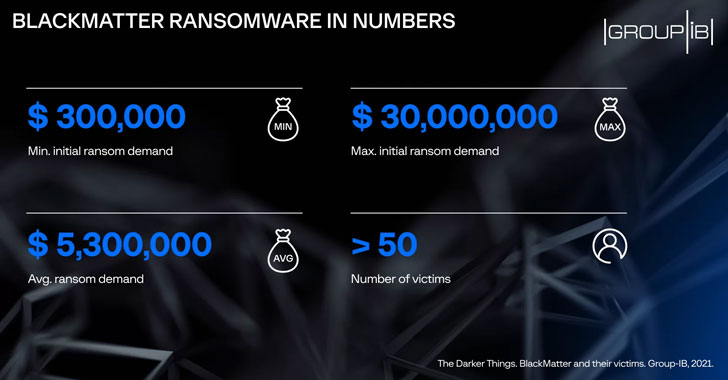
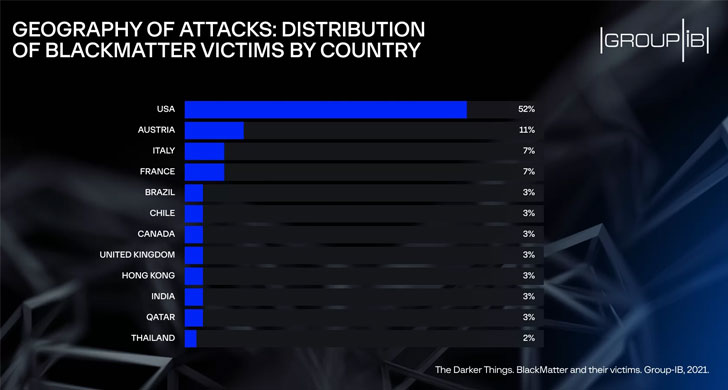
BlackMatter emerged in July 2021 boasting of incorporating the “best features of DarkSide, REvil, and LockBit” and is considered the successor to DarkSide, which has since shut down alongside REvil in the wake of law enforcement scrutiny. Operating as a ransomware-as-a-service (RaaS) model, the BlackMatter is believed to have hit more than 50 companies in the U.S., Austria, Italy, France, Brazil, among others.
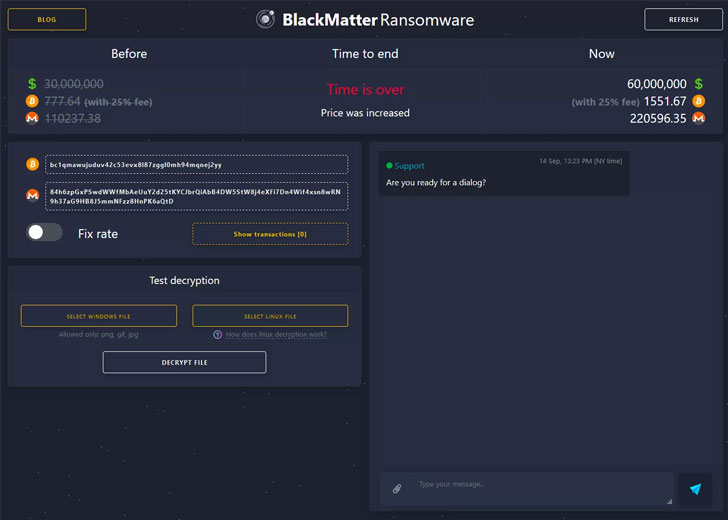
What’s more, the threat actor creates a unique Tor chat room for communication for each victim, a link to which is attached to the text file containing the ransom demand. BlackMatter is also known to double the ransom amount when the ultimatum expires, before moving to publish the stolen documents in the event the victim refuses to pay up.
According to security researchers from Microsoft’s counter-ransomware unit, DarkSide and its BlackMatter rebrand is the handiwork of a cybercrime group tracked as FIN7, which was recently unmasked operating a front company named Bastion Secure to lure tech professionals with the goal of launching ransomware attacks.
“When other parameters are set or any parameters are absent, the system is fully encrypted according to the configuration settings,” Zhdanov noted. “Upon completing the encryption, the ransomware creates a BMP image alerting that files have been encrypted, which it then sets as the desktop wallpaper. Starting from version 1.4, the ransomware can also print the text of the demand for ransom on the victim’s default printer.”
The Linux variants, on the other hand, are designed to target VMware ESXi servers, featuring the ability to terminate virtual machines and kill specific processes, including the firewall, prior to commencing data encryption.
The findings come as VX-Underground, a portal that hosts malware source code, samples and papers, revealed that the group is pulling the plug on its operations “following pressure from local authorities.” The post shared on the RaaS website also noted that a “part of the team is no longer available, after the latest news.”
It’s not immediately clear what the “latest news” could be referring to, but it implies a strong link to the coordinated international law enforcement operation late last month that saw 12 individuals arrested for orchestrating ransomware attacks against 1,800 victims across 71 countries since 2019.
In an advisory issued on October 18, 2021, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the National Security Agency (NSA) warned that the BlackMatter ransomware group has targeted “multiple” organizations deemed critical infrastructure, including two entities in the U.S. food and agriculture sector.