Enterprise software provider Zoho on Friday warned that a newly patched critical flaw in its Desktop Central and Desktop Central MSP is being actively exploited by malicious actors, marking the third security vulnerability in its products to be abused in the wild in a span of four months.
The issue, assigned the identifier CVE-2021-44515, is an authentication bypass vulnerability that could permit an adversary to circumvent authentication protections and execute arbitrary code in the Desktop Central MSP server.
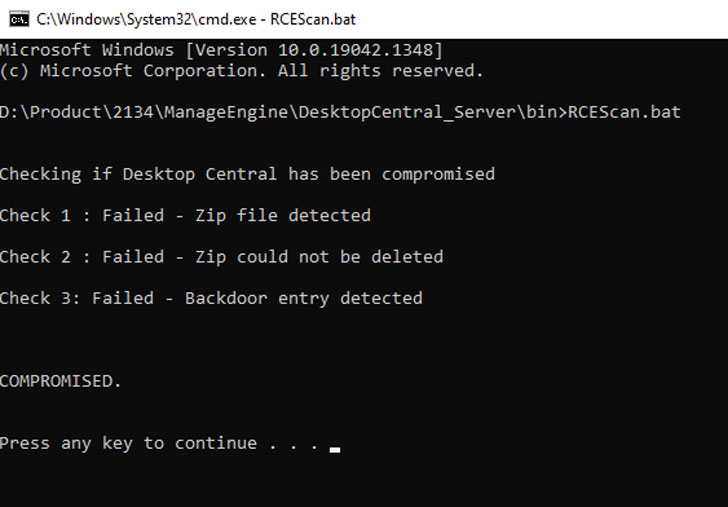
“If exploited, the attackers can gain unauthorized access to the product by sending a specially crafted request leading to remote code execution,” Zoho cautioned in an advisory. “As we are noticing indications of exploitation of this vulnerability, we strongly advise customers to update their installations to the latest build as soon as possible.”
The company has also made available an Exploit Detection Tool that will help customers identify signs of compromise in their installations.
With this development, CVE-2021-44515 joins two other vulnerabilities CVE-2021-44077 and CVE-2021-40539 that have been weaponized to compromise the networks of critical infrastructure organizations across the world.
The disclosure also comes a day after the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned that CVE-2021-44077 — an unauthenticated, remote code execution vulnerability affecting ServiceDesk Plus — is being exploited to drop web shells and carry out an array of post-exploitation activities as part of a campaign dubbed “TiltedTemple.”