As many as 1.6 million WordPress sites have been targeted by an active large-scale attack campaign originating from 16,000 IP addresses by exploiting weaknesses in four plugins and 15 Epsilon Framework themes.
WordPress security company Wordfence, which disclosed details of the attacks, said Thursday it had detected and blocked more than 13.7 million attacks aimed at the plugins and themes in a period of 36 hours with the goal of taking over the websites and carrying out malicious actions.
The plugins in question are Kiwi Social Share (<= 2.0.10), WordPress Automatic (<= 3.53.2), Pinterest Automatic (<= 4.14.3), and PublishPress Capabilities (<= 2.3), some of which have been patched dating all the way back to November 2018. The impacted Epsilon Framework themes and their corresponding versions are as follow —
- Activello (<=1.4.1)
- Affluent (<1.1.0)
- Allegiant (<=1.2.5)
- Antreas (<=1.0.6)
- Bonkers (<=1.0.5)
- Brilliance (<=1.2.9)
- Illdy (<=2.1.6)
- MedZone Lite (<=1.2.5)
- NatureMag Lite (no known patch available)
- NewsMag (<=2.4.1)
- Newspaper X (<=1.3.1)
- Pixova Lite (<=2.0.6)
- Regina Lite (<=2.0.5)
- Shapely (<=1.2.8)
- Transcend (<=1.1.9)
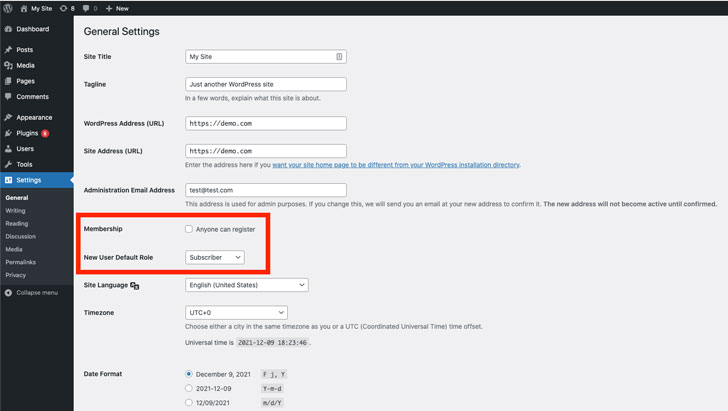
Most of the attacks observed by Wordfence involve the adversary updating the “users_can_register” (i.e., anyone can register) option to enabled and setting the “default_role” setting (i.e., the default role of users who register at the blog) to administrator, thereby allowing an adversary to register on the vulnerable sites as an administrator and seize control.
What’s more, the intrusions are said to have spiked only after December 8, indicating that “the recently patched vulnerability in PublishPress Capabilities may have sparked attackers to target various Arbitrary Options Update vulnerabilities as part of a massive campaign,” Wordfence’s Chloe Chamberland said.
In light of active exploitation, WordPress site owners running any of the aforementioned plugins or themes are recommended to apply the latest fixes to mitigate the threat.