Researchers have disclosed security vulnerabilities in handover, a fundamental mechanism that undergirds modern cellular networks, which could be exploited by adversaries to launch denial-of-service (DoS) and man-in-the-middle (MitM) attacks using low-cost equipment.
The “vulnerabilities in the handover procedure are not limited to one handover case only but they impact all different handover cases and scenarios that are based on unverified measurement reports and signal strength thresholds,” researchers Evangelos Bitsikas and Christina Pöpper from the New York University Abu Dhabi said in a new paper. “The problem affects all generations since 2G (GSM), remaining unsolved so far.”
Handover, also known as handoff, is a process in telecommunications in which a phone call or a data session is transferred from one cell site (aka base station) to another cell tower without losing connectivity during the transmission. This method is crucial to establishing cellular communications, especially in scenarios when the user is on the move.
The routine typically works as follows: the user equipment (UE) sends signal strength measurements to the network to determine if a handover is necessary and, if so, facilitates the switch when a more suitable target station is discovered.
While these signal readings are cryptographically protected, the content in these reports is themselves not verified, thus allowing an attacker to force the device to move to a cell site operated by the attacker. The crux of the attack lies in the fact that the source base station is incapable of handling incorrect values in the measurement report, raising the possibility of a malicious handover without being detected.
The new fake base station attacks, in a nutshell, render vulnerable the handover procedures, which are based on the aforementioned encrypted measurement reports and signal power thresholds, effectively enabling the adversary to establish a MitM relay and even eavesdrop, drop, modify, and forward messages transmitted between the device and the network.
“If an attacker manipulates the content of the [measurement report] by including his/her measurements, then the network will process the bogus measurements,” the researchers said. “This is possible by imitating a legitimate base station and replaying its broadcast messages.”
“Attracting” the device to a fake base station
The starting point of the attack is an initial reconnaissance phase wherein the threat actor utilizes a smartphone to collect data pertaining to nearby legitimate stations and then uses this information to configure a rogue base station that impersonates a genuine cell station.
The attack subsequently involves forcing a victim’s device to connect to the false station by broadcasting master information block (MIB) and system information block (SIB) messages — information necessary to help the phone connect to the network — with a higher signal strength than the emulated base station.
In tricking the UEs to connect to the imposter station and forcing the devices to report bogus measurements to the network, the goal is to trigger a handover event and exploit security flaws in the process to result in DoS, MitM attacks, and information disclosure affecting the user as well as the operator. This not only compromises users’ privacy but also puts service availability at risk.
“When the UE is in the coverage area of the attacker, the rogue base station has high enough signal power to ‘attract’ the UE and trigger a [measurement report], then the attacker has very good chances of forcing the victim UE to attach to his/her rogue base station [by] abusing the handover procedure,” the researchers explained.
“Once, the UE is attached to the attacker it could either enter in a camped mode due to a denial-of-service (DoS) attack and become unresponsive, or the attacker could establish a man-in-the-middle (MitM) relay building the basis for other advanced exploits.”
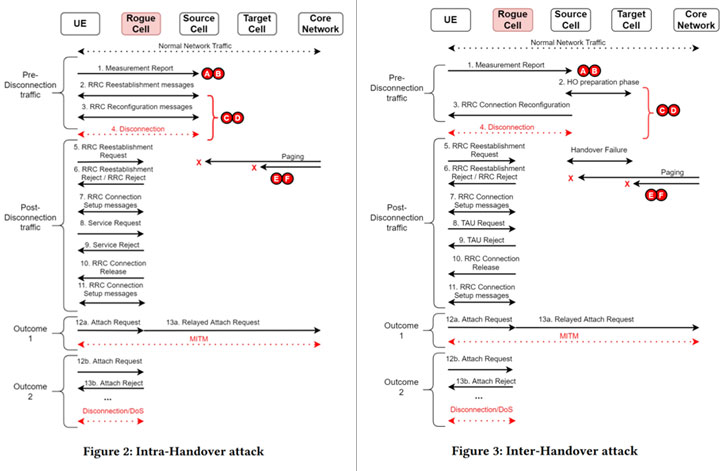
As many as six security vulnerabilities (identified from A to F in the image above) have been identified in the handover process —
- Insecure broadcast messages (MIB, SIB)
- Unverified measurement reports
- Missing cross-validation in the preparation phase
- Random-access channel (RACH) initiation without verification
- Missing recovery mechanism, and
- Difficulty of distinguishing network failures from attacks
In an experimental setup, the researchers found all the test devices, including OnePlus 6, Apple iPhone 5, Samsung S10 5G, and Huawei Pro P40 5G, to be susceptible to DoS and MitM attacks. The findings were presented at the Annual Computer Security Applications Conference (ACSAC) held earlier this month.