A group of researchers has revealed details of a new vulnerability affecting Intel CPUs that enables attackers to obtain encryption keys and other secret information from the processors.
Dubbed ÆPIC Leak, the weakness is the first-of-its-kind to architecturally disclose sensitive data in a manner that’s akin to an “uninitialized memory read in the CPU itself.”
“In contrast to transient execution attacks like Meltdown and Spectre, ÆPIC Leak is an architectural bug: the sensitive data gets directly disclosed without relying on any (noisy) side channel,” the academics said.
The study was conducted by researchers from the Sapienza University of Rome, the Graz University of Technology, Amazon Web Services, and the CISPA Helmholtz Center for Information Security.
The vulnerability (CVE-2022-21233, CVSS score: 6.0), which affects CPUs with Sunny Cover microarchitecture, is rooted in a component called Advanced Programmable Interrupt Controller (APIC), which provides a mechanism to handle and route hardware interrupt signals in a scalable manner.
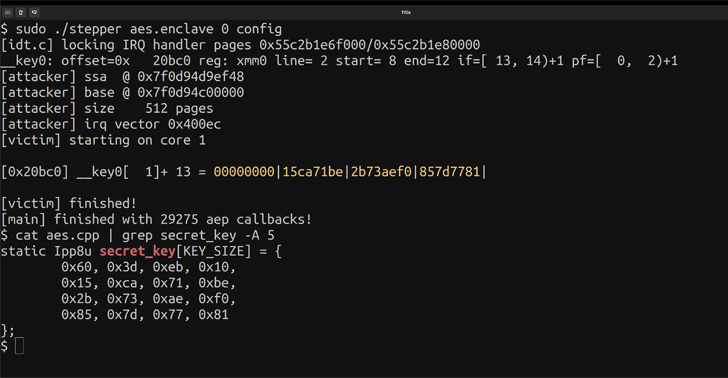
“The scan of the I/O address space on Intel CPUs based on the Sunny Cove microarchitecture revealed that the memory-mapped registers of the local Advanced Programmable Interrupt Controller (APIC) are not properly initialized,” the researchers noted.
“As a result, architecturally reading these registers returns stale data from the microarchitecture. Any data transferred between the L2 and the last-level cache can be read via these registers.”
ÆPIC Leak specifically targets systems using Intel’s trusted execution environment (TEE) known as Software Guard eXtensions (SGX), causing the leakage of AES and RSA keys from secure enclaves that run on the same physical CPU core with a success rate of 94% and 74% respectively.
“By protecting selected code and data from modification, developers can partition their application into hardened enclaves or trusted execution modules to help increase application security,” Intel explains about the security assurances offered by SGX.
The flaw, put simply, breaks the aforementioned guarantees, enabling an attacker with permissions to execute privileged native code on a target machine to extract the private keys, and worse defeat attestation, a cornerstone of the security primitives used in SGX to ensure the integrity of code and data.
In response to the findings, Intel has released firmware updates, while describing the issue as a medium-severity vulnerability related to improper isolation of shared resources, leading to information disclosure via local access.
It’s also worth noting that Intel has since deprecated support for SGX for its client CPUs, what with a litany of attack methods plaguing the technology, including SGX-ROP, MicroScope, Plundervolt, Load Value Injection, SGAxe, and VoltPillager.
SQUIP Side Channel Attack Affect AMD CPUs
The development comes as researchers demonstrated what’s the first-ever side channel attack (CVE-2021-46778) on scheduler queues impacting AMD Zen 1, Zen 2, and Zen 3 microarchitectures that could be abused by an adversary to recover RSA keys.
The attack, codenamed SQUIP (short for Scheduler Queue Usage via Interference Probing), entails measuring the contention level on scheduler queues to potentially glean sensitive information.
No security updates have been released to patch the line of attack, but the chipmaker has recommended that “software developers employ existing best practices, including constant-time algorithms and avoiding secret-dependent control flows where appropriate.”