Security teams typically have great visibility over most areas, for example, the corporate network, endpoints, servers, and cloud infrastructure. They use this visibility to enforce the necessary security and compliance requirements. However, this is not the case when it comes to sensitive data sitting in production or analytic databases, data warehouses or data lakes.
Security teams have to rely on data teams to locate sensitive data and enforce access controls and security policies. This is a huge headache for both the security and data teams. It weakens the business’s security and compliance putting it at risk of exposing sensitive data, large fines, reputational damages, and more. Also, in many cases, it slows down the business’s ability to scale up data operations.
This article examines how Satori, a data security platform, gives control of the sensitive data in databases, data warehouses and data lakes to the security teams.
Satori’s automated data security platform provides a simple and easy way to meet security and compliance requirements while reducing risk exposure.
Why is Securing Data Stores Hard?
Security teams don’t have good visibility and enforcement of policies regarding access to DBs, data warehouses or data lakes. Take a look at an example.
Nick is a security engineering manager at ACME organization. He is responsible for keeping up with changing security and compliance regulations such as HIPAA, SOC2, and ISO. This is a difficult task since security and compliance regulations are always changing and evolving. Nick is good at his job and can wade through the complexities of the different regulations and determine the necessary security measures to ensure that ACME remains in compliance. This is important so that ACME doesn’t fail an audit, expose sensitive data, receive fines or worse.
Then, one day, Nick is suddenly tasked with meeting security and compliance requirements across all of ACME’s analytic and production data.
Nick faces a problem. Although he has done his job and determined the necessary steps to ensure security and compliance it is very difficult to actually carry out these steps and implement the security policies. There are several reasons why Nick’s job is difficult and frustrating that are explored in more detail below.
Visibility Over Sensitive Data and Logs
Nick’s lack of visibility limits his ability to implement and manage security policies and compliance requirements. Three main sources impede his visibility.
1 — Different logs from different sources are “buried.”
Since ACME has sensitive data spread across multiple databases, data lakes and data warehouses; there are a wide variety of audit logs from all of these different sources. Furthermore, Nick has to correlate the log data with known locations of sensitive data (if he has them).
2 — Changes to the configuration and processes to enable visibility.
It is important to ensure that all sensitive data access is accurately monitored. Nick may want to examine why a user was accessing sensitive information in a region outside their service area and prevent this type of access from occurring in the future. He needs to change the configuration and make sure that the change control processes are effective. However, this is not as simple as it seems. The lack of visibility means that Nick cannot verify that these changes are made in real-time.
3 — Knowing the type and location of sensitive data.
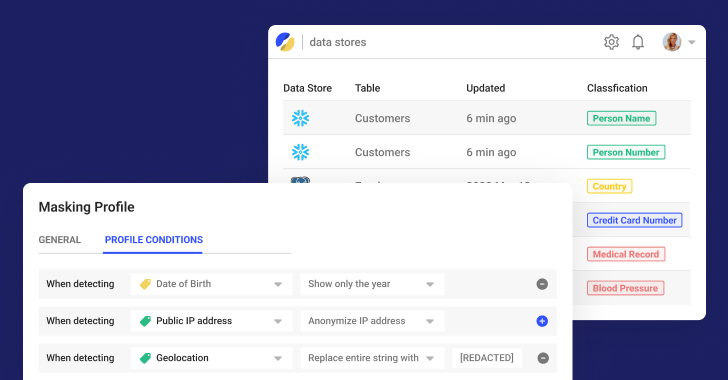
Nick doesn’t have the ability to continuously seek out sensitive data. His lack of visibility coupled with the fact that he is not the owner of these data stores means that he is not able to search the multiple data stores for sensitive data. Instead, he has to rely on the engineering team.
The majority of companies use manual processes to scan and discover sensitive data. The manual scanning of data, when Nick can get the data engineers to stop their projects and undertake this task, is slow and error-prone. This means that Nick is often anxious about getting the data engineers to continuously scan the data to find sensitive information and identity information.
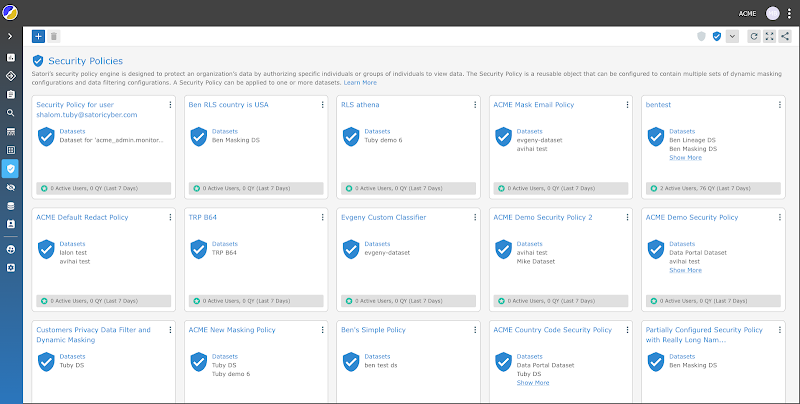
Enforcement of Security Policies
ACME has sensitive data that is spread across a number of diverse databases, data lakes and data warehouses. Nick is a very good security engineer but it is unlikely that he has the knowledge to understand SQL and the inner workings of the databases, data warehouses and lakes that comprise the ACME data stack. Since he does not have the ability to actually code the necessary changes to the security policies he has to rely on the data engineers to carry out his tasks.
Even though data engineers typically prefer to work on their own projects instead of implementing Nick’s security policies, it is unlikely that they would allow Nick to implement them himself, even if he knew how. The engineers who own the data stores probably do not want Nick to meddle with things like creating objects or changing configurations on their data stores. So even if he wanted to, and could, it is unlikely that Nick has the access to apply and implement the necessary security policies, instead, he needs to rely on the data engineers to do this for him.
Using a Data Security Platform
An overview of using Satori’s automated data security platform, to overcome such challenges follows.
Full Visibility
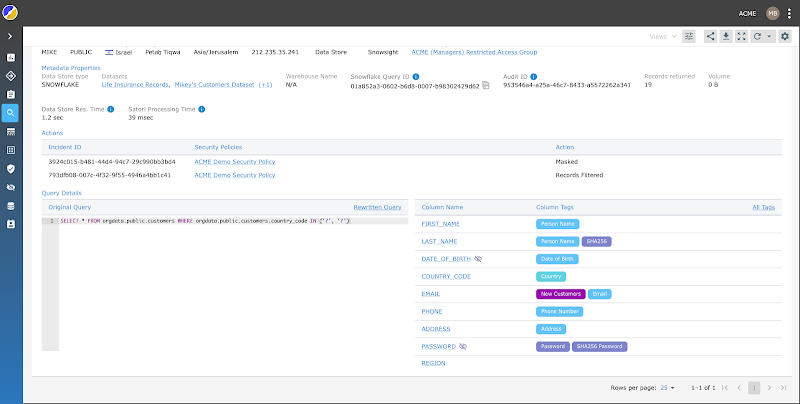
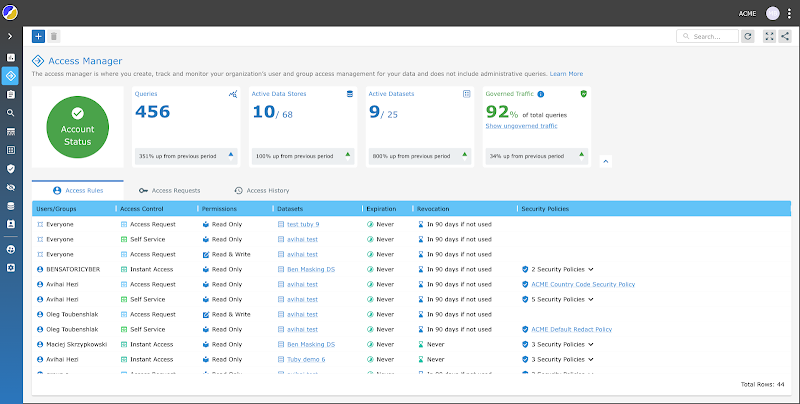
Nick can use Satori’s Access Manager and gain full visibility over all of the implemented security policies and audit logs from analytics and production data.
Now Nick can see who accessed which sensitive data and when in a single frame. He can view all data access and audit logs across all platforms, so sensitive data access is no longer “buried”. Nick can also see which security policies have been applied and easily update the security policies and access requirements.
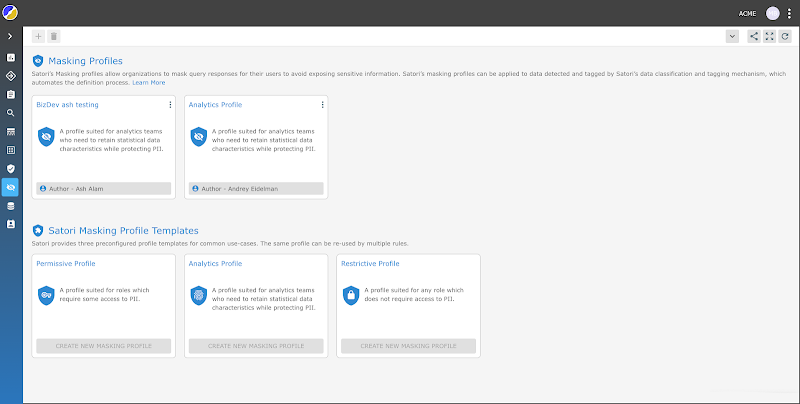
Implementing Security and Compliance Policies
Satori is easily implemented and can get Nick up and running across ACME’s databases, data warehouses and lakes in days or hours instead of months.
This is because Satori does not change anything in ACME’s data stores, so there is no additional coding necessary, or changes to the data; only the security policies and requirements need to be applied.
Check how easy it is to set and implement security policies and compliance requirements with Satori and take a test drive.
Fully Automated
Satori automates the process of finding and classifying sensitive data, applying the applicable security policies, and then granting and revoking access controls. The ability to automatically find sensitive data is invaluable to Nick because he is not the actual owner of the databases, data warehouses or lakes where the data is stored.
Nick now can control the implementation of security policies, when regulations are updated, and we all know this happens. He can quickly and easily implement the updated requirements and reduce the likelihood of failing an audit or worse.
Nick is happy because he can easily implement the necessary requirements. The data users are happy because using Satori increases the level of security, but doesn’t change or delay their user experience. As a bonus, the data engineers are also happy because they don’t have to worry about Nick’s nagging to constantly update and implement security policies.
Is a Data Security Platform a Good Fit?
Not everyone requires a data security platform, in some cases, it is simpler and easier to continue with business as usual. However, if a business has any of the following conditions, then a data security platform is required to secure data.
- Sensitive data
- Multiple data users
- Multiple databases, data warehouses or data lakes
Satori’s Data Security Platform
Satori’s automated data security platform helped Nick gain ownership over the data he is responsible for. This enabled him to focus on the security and compliance parts of his job. Nick can automate all processes from searching out sensitive data to applying and enforcing security policies. He always has full visibility of data access and can review the audit and security logs quickly and easily.
To try Satori for yourself, take a test drive or book a demo meeting with Satori.